
WEP File Analyzer is a Trace File Decrypter.
This is a complex but very handy tool. It can be used to decrypt
WEP'ed trace files off-line. This permits access to trace files
that were captured via a tool that does not support WEP, and to
data that was captured at a time when the WEP key(s) were not known.
This WEP File Analyzer can be used in complement
to WinAirsnort program for example.
IMPORTANT! This software performs WEP decryption and Analysis,
not WEP key recovery. This is not a cracking tool ! The session
keys must be known and input to the program before decryption can
successfully occur.
WEP Security Key Background :
The Wired Equivalent Privacy protocol (WEP) is the standard for
authentication and encryption used in the 802.11b wireless Ethernet
protocol. For encryption, WEP uses the RC4 algorithm.
The WEP algorithm protects wireless communication from eavesdropping.
WEP prevents unauthorized access to a wireless network. WEP relies
on a secret key shared between a laptop with wireless Ethernet card
(or mobile station) and an access point (the base station). The
WEP secret key encrypts packages before they are transmitted. WEP
uses an integrity check to prevent packets being modified in transit.
Most installations use a single WEP key between the mobile stations
and access points. Multi WEP key techniques in network management
enhance the security.
WEP encryption is the translation of data into a secret code. The
WEP encryption key is used to provide wireless clients with confidentiality
and authentication in an IEEE 802.11 b environment. WEP encryption
is the most effective way to achieve data security. To read a WEP
encryption on file you need a secret key or password to decrypt
it. Unencrypted data is called plain text, the cipher text refers
to encrypted text. There are two main types of WEP encryption, asymmetric
WEP encryption or public key WEP encryption and symmetric WEP encryption.
To preserve confidentiality, WEP encryption uses RC4 encryption
for the 802.11 frame with shared keys. WEP encryption uses the RC4
encryption method and the conversion of plain text, cipher text
and the initialization vector (IV) that is used to turn the plain
text into cipher text. This can in turn be decoded into the RC4
keystream. WEP encryption depends on a shared key, its distribution
and the WEP encryption algorithm. The WEP encryption standard employs
40-bit encryption as well as a 128-bit WEP encryption option. Some
WEP wireless vendors offer both WEP encryption options. By using
the 128-bit keys, WEP encryption ensures that your data is as secure
as unencrypted wired Ethernet.

Data Engine :
Enter the WEP Keys. Enter the keys to be used to decrypt data
frames contained in the file. You must know the keys in advance.
The WEP File Analyzer will not recover keys automatically. The default
is 64-bit encryption. To enable 128-bit operation, check the box
labelled "128-Bit" next to the key entry field. The entry
box will expand to permit the entry of the larger keys. WEP keys
are made up of HEX digits. The characters "0123456789ABCDEF"
are all valid HEX digits. 64-bit keys are comprised of 10 HEX digits.
128-bit keys are comprised of 26 HEX digits.
WEP Key setting is set to :
- Key1 : 64-bit or 128-bit Key
- Key2 : 64-bit or 128-bit Key
- Key3 : 64-bit or 128-bit Key
- Key4 : 64-bit or 128-bit Key
Start Decryption.
Select the start button to begin the decryption process. WEP Decryption
Steps are following :
_ Use key number to get private key
_ Use sent IV to generate keystream
_ RC4(IV,Key)
_ XOR received ciphertext with keystream
_ Get ICV+Payload
_ Compute ICV on Payload
_ If new ICV then sent ICV, then the packet is good
WEP Encryption Panel Encryption WEP Key setting is set to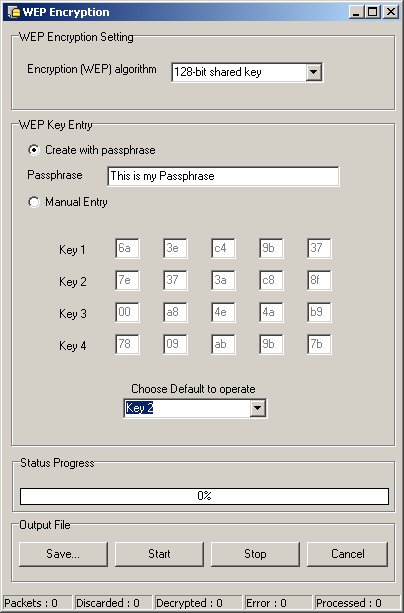
- 64-bit shared Key
- 128-bit shared Key
- 256-bit shared Key
WEP Key Entry (Passphrase or Manual Entry)
WEP File Analyzer asks the user to enter a phrase and generates
a full 64 to 256-bit key based on this phrase, saving the user from
manual key entry.
Manual Entry
One to four encryption keys must be entered in the panel. These
keys will be used to encrypt data file. The format of entering the
key values is either in textual format or in hexadecimal format
(an entry starting with "0x" will be interpreted as Hexadecimal).
A text string is translated in the ASCII values associated with
each character.
The user must assign one of the entered keys as the designated key
for encrypting all packet transmission. This is done by selecting
the appropriate number from the pull-down list "Choose Default
to operate".
Export (save) files in the following format : LibPCap file
format *.cap, Microsoft Network Monitor Format (*.Cap), Network
Associates Sniffer (DOS) Format (*.Enc), Network General's NetX'Ray
Format (*.Cap), RFC 1761 Snoop Format (*.Snp)
Import (load) trace files data in the following format :
*.lfc; *.enc; *.snp
Import WinAirsnort Trace File data in the following format : *.Trc
WEP Point Configuration Panel
Enter the WEP Keys.
Enter the keys into hexadecimal format (0-9 and A-F) to be used
to decrypt data frames contained in the file. You must know the
keys in advance. WEP keys are made up of HEX digits. The characters
"0123456789ABCDEF" are all valid HEX digits. 64-bit keys
are comprised of 10 HEX digits. 128-bit keys are comprised of 26
HEX digits. WEP Key setting is set to :
- Key1 : Check CRC checksum for that key (CC1)
- Key2 : Check CRC checksum for that key (CC2)
- Key3 : Check CRC checksum for that key (CC3)
- Key4 : Check CRC checksum for that key (CC4)
Initial Vector Analyzer (IV) Panel
An 802.11b frame is composed of a header which contains information
specific to the 802.11b protocol (source/destination MAC address,
type of frame, etc.) as well as a payload. The payload contains
a IP header, a TCP header, and a data payload. When encrypting a
frame, the first step is creating an Initial Chaining Vector (ICV),
and appending this ICV to the end of the payload. The ICV is simply
a 32-bit CRC of the payload contents. After the ICV is created,
a 24-bit Initialization Vector (IV) is generated.
The IV is used to initialize the RC4 algorithm prior to encryption.
One of four encryption keys (40 bits each, stored on the client)
is then selected and this key number (8 bits) is appended to the
IV. In many implementations of WEP,
the user can instead chose to use a single 104-bit key for better
encryption. It is important to note that most keys are generated
by software included with the 802.11b card. The software asks the
user toenter a phrase and generates a full 40 or 104 bit key based
on this phrase, saving the user from manual key entry. Often, client
software will list a choice between 64 or 128 bit encryption. This
simply refers to the size of the key plus the size of the IV - the
key size remains 40 or 104 bits, respectively.
Using the IV and key, the RC4 cipher is initialized and its output
XOR-ed with the cipher text. A plaintext frame and ICV are the output.
As a final check, the CRC of the plaintext payload is re-calculated
and compared to the original CRC stored in the ICV.
Select The Initial Vector Stream
Select a 32-bit Initial Chaining Vector Stream and a 24-bit Initial
Vector stream. Using the IV and key, the RC4 cipher is initialized
and its output XOR-ed with the cipher text.
| Download Free documentation |
| Product |
Platform |
File Size |
Download |
|
WEP File Analyzer
The Advanced binary File Editor for WEP encrypted
Files.
|
 Win 98, ME, NT, Win 98, ME, NT,
2000, XP. |
950 kB |
|
 WEP File
Analyzer is compatible with Windows 98, ME, NT, 2000 and
XP WEP File
Analyzer is compatible with Windows 98, ME, NT, 2000 and
XP
|



